Fast and reliable interception
for Incoming and Outgoing encrypted GSM communication
 |
| Description: Fast and reliable interception, interrogation and jamming of GSM traffic • Interception for Incoming and Outgoing encrypted GSM communication
including A5/1 in real-time and without cooperation with network operators |
1. Introduction 2. System overview Complex consists of following parts: |
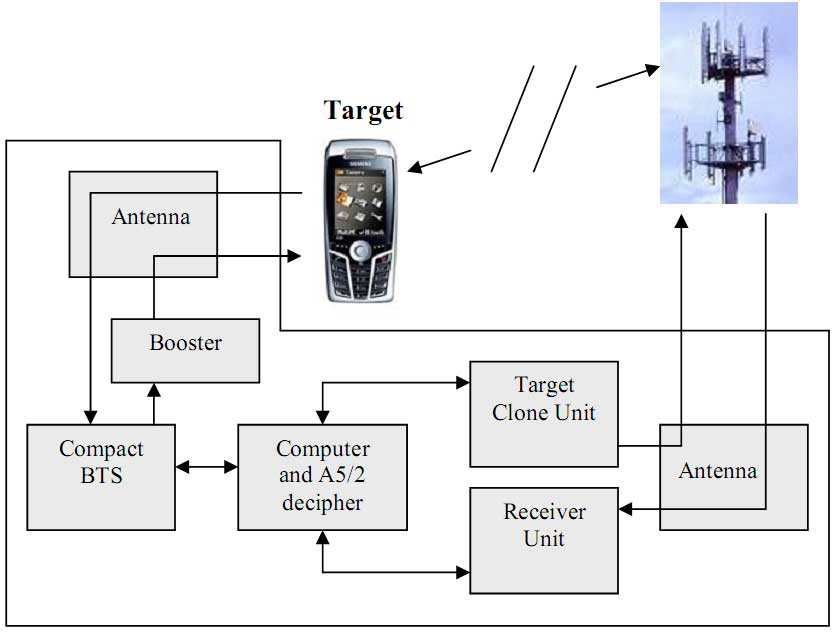 |
3. Operational overview It is a true Man-In-The-Middle (MitM) attack on GSM communication which is fully implemented in the SYSTEM. 5. What is in the package? 6. Comparison between SYSTEM and other known active systems in the market |
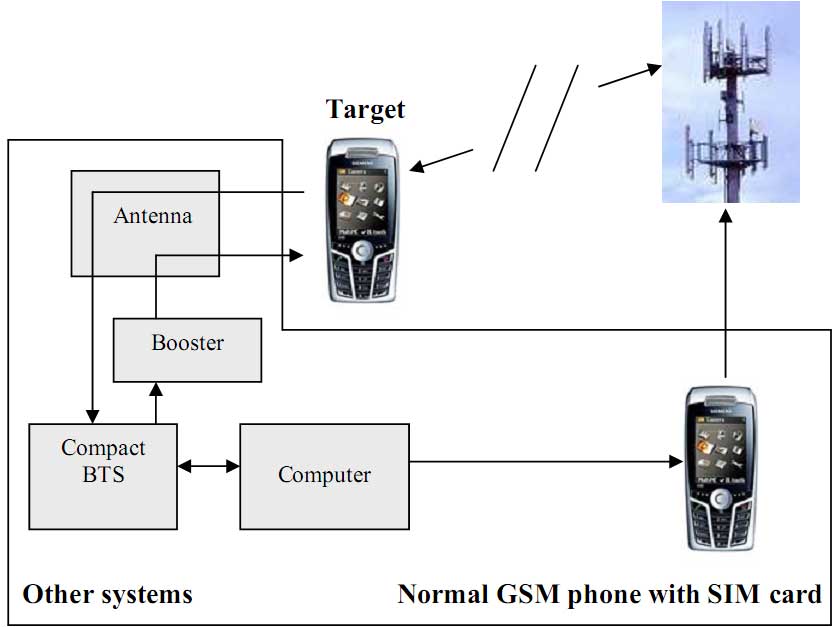 |
Not having such features all other active systems are only able to force mobile phones to register with faked BTS and identify themselves. While operating well as IMSI/IMEI catchers they are not able to efficiently intercept communication. |
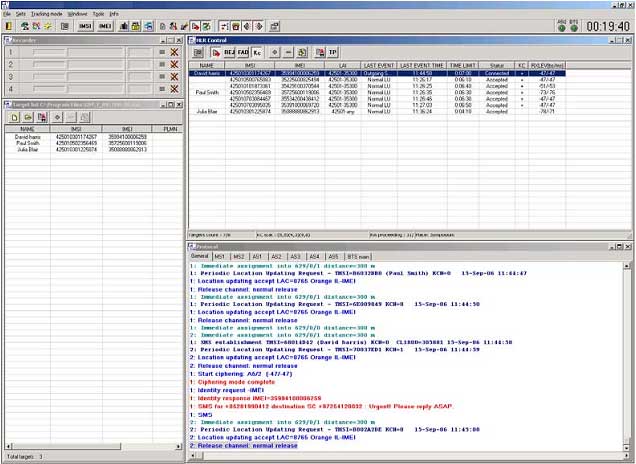 Main screen |
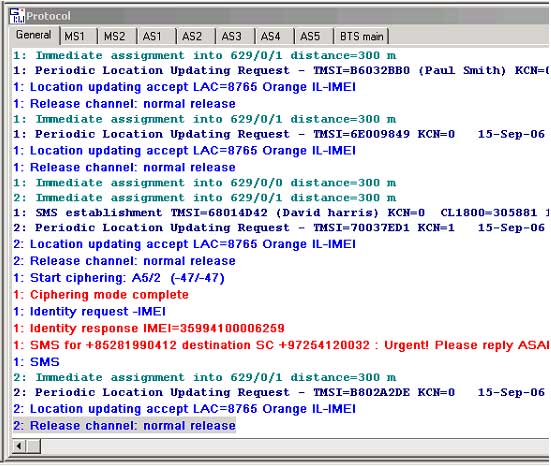 Protocol screen |
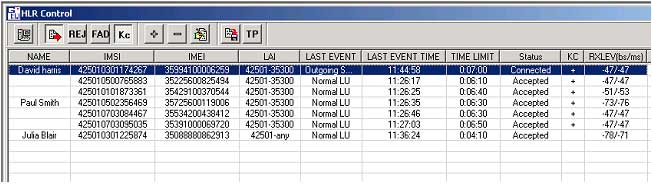 HLR screen |
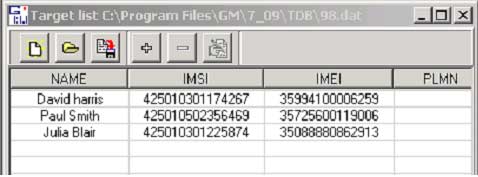 Target list screen |
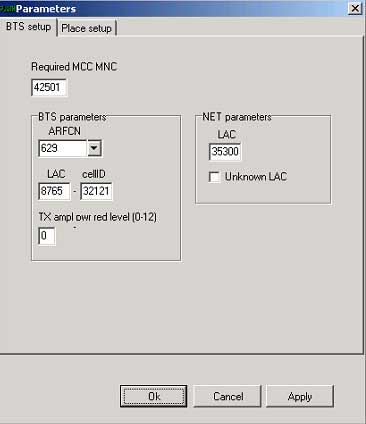 Parameters screen |
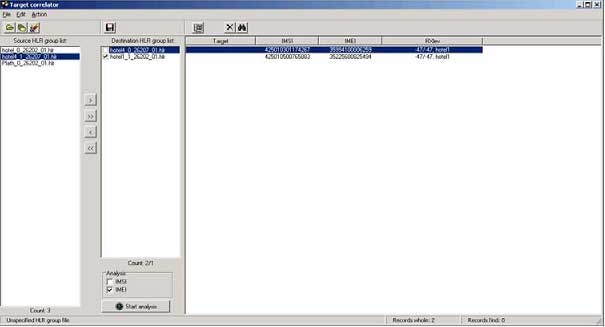 Cross-compare screen |
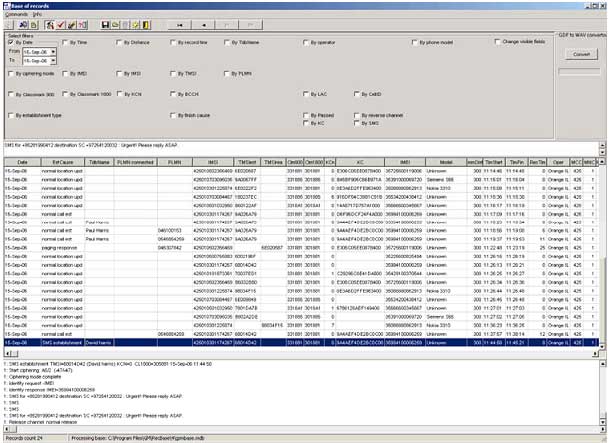 Data Base Screen |
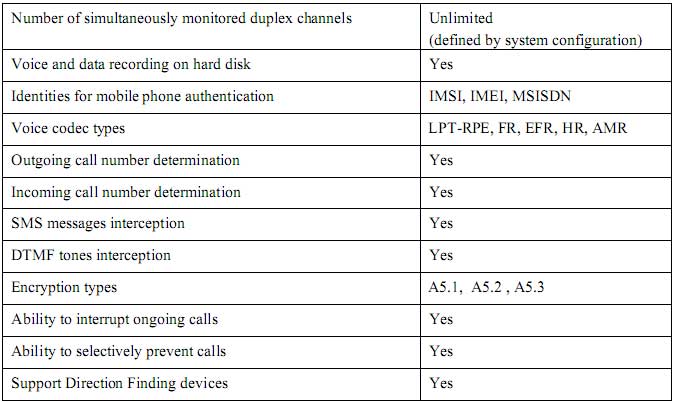
8. System features, Technical and Operational Characteristics |
|
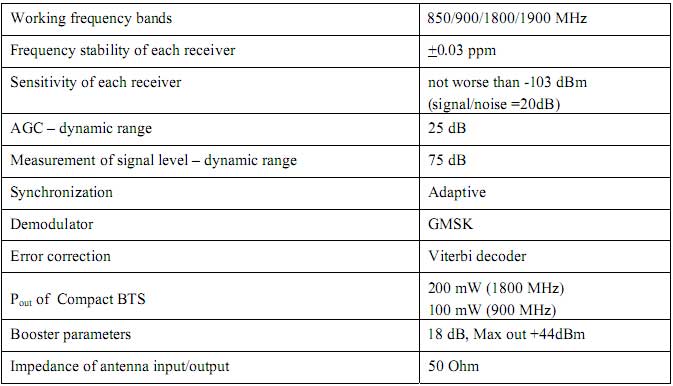 Technical Characteristics |