|
|
Overview and screen shoots |
| |
|
Fig.1 Main screen |
| |
| The main operation screen (Fig.1) is divided into 4 main parts: |
| - receivers window |
| - tape recorder window |
| - target list / base stations list |
| - protocol window |
| |
|
Fig.2 Receivers window |
|
| 1. Receiver number. |
| 2. Channel/Timeslot number. |
| 3. Receiver status. |
|
- Traffic channel |
|
- Control channel |
| 4. Signal level indicator of forward and reverse channels |
|
- Forward channel
- Reverse channel |
| 5. Identity of intercepted call or name of the network operator |
| |
| A double click on the receiver number will open the Receivers setup screen. |
|
Fig.3 Receivers setup screen |
| |
|
Fig.4 Target List |
| |
|
Fig.5 Target List Edit window |
| |
|
Fig.6 Base Stations List |
| |
|
Fig.7 Tape Recorder Window |
| 1. Receiver number |
| 2. Voice Record Level Indicator |
| 3. TMSI or IMSI number |
| 4. Duration |
| 5. Reset Call button |
| 6. Pause button |
| 7. Speaker ON/OFF button |
| |
|
Fig.8 Protocol Window |
| 1. Receiver number |
| 2. GSM network events |
| |
Operational modes |
| |
|
Fig.9 Toolbar |
| |
| The system has 7 main operational modes: |
| - Random Mode |
| - Classmark mode |
| - IMSI/TMSI mode |
| - Distance mode |
| - Phone number mode |
| - Reverse channel mode |
The additional operational modes are used together with main modes.
The additional modes can be used together in any combination. |
| - Capture the secret KI code off air |
| - intercept and display SMS, fax, and email |
| - tracking system with near GPS accuracy. Even when the target is inside buildings |
| - intercept calls made in another country |
| |
Main Operational Modes |
| |
| Random Mode |
| This mode is usually used to intercept all calls to or from a given area if the particular phone number is unknown. |
| |
| Classmark Mode |
| All mobile phones are distinguished by their classmarks. The classmark is one of the characteristics of mobile phones which is never changed. As soon
as some phone conversation is intercepted, the classmark of the active phone is displayed in the protocol window and can be put on the target list. Subsequently, this parameter can be used for monitoring calls made from or to the specific mobile phone. |
| |
| IMSI/TMSI Mode |
| The real mobile phone number is never transmitted over the air in GSM networks. Instead of phone numbers, GSM networks use special identities (IMSI or TMSI) for mobile phone authentication. |
| Using a special technique, the system discovers the identity that corresponds to the particular phone number. These identities are stored in the target list and used for monitoring by specific phone number (see Fig.5). |
| One of these identities (TMSI) is changed from time to time. The system automatically follows all TMSI modifications and automatically updates them in the Target List without intervention of the system operator. |
| |
| Distance mode |
This mode allows interception of those conversations, and only those conversations, being made to or from mobile phones located at a given distance from Base Stations.
The distance can be specified in the Receiver Setup Screen (see Fig.3). |
| This mode may be used effectively when there is some “Place of Interest” and there are no particular phone numbers or other information about mobile phones for that place. |
| |
| Reverse Mode |
| When reverse mode is active, only conversations with active reverse channel (i.e. from mobile phones located near the Interceptor) will be intercepted. |
| This mode can be very useful for interception of calls being made to or from a specific area when the Interceptor is in the area. |
| Another very effective implementation is a combination of (main) Random Mode and (additional) Distance and Reverse Modes together with a
unidirectional antenna. In this case a “Place of Interest” can be defined very closely, in
terms of distance from one side and by azimuth from other side. |
| |
| Phone Number Mode |
| When this mode is active, the only calls intercepted will be calls made from or to a phone number defined in the Target List (see Fig.5 Target List Edit window). |
| |
| IMEI mode |
| Some GSM networks use IMEI identity. This parameter can be very useful as it’s a characteristic of mobile phones which is never changed. |
| In addition, this identity contains the model of the mobile phone. If IMEI is used by the GSM network, Interceptor will display models of mobile phones in the Protocol Window. |
| |
| Capture the secret KI code off air |
| The security of the whole GSM security model is based on the secret Ki. If this key is compromised the whole account is compromised.
Once the attacker is able to retrieve the Ki, he can not only listen to the subscribers calls, but also place calls billed to the original subscriber's account because he can now impersonate the legitimate subscriber.
However the GSM network has trip wires for this: If two phones with the same ID are powered at the same time, the GSM network notices this, makes a location query for the phones, notices that the 'same' phone is in two different locations at the same time, and closes the account, thus preventing the attacker and the legitimate subscriber from placing calls But this is not relevant if the attacker is only interested in listening to the calls of the subscriber, as is assumed in this paper. In this case, the attacker can stay passive and just listen to the call, thus staying invisible to the GSM network.
|
| All other passive systems need to know the targets KI before monitoring can begin. The operator can get this either by brute force reading the SIM card, (provided you get the correct PIN code) or by getting the code from the network/airtime provider.
However, many organizations would prefer not to inform other parties of their actions, and for these agencies our new feature is extremely valuable. The operator will be totally independent in acquiring the vital KI code with our new unit.
The GSM Interceptor is the first and only unit in the world to be able to extract the 15 digit encrypted KI code off air. This can be done either by using the main unit itself, or with the small black box which comes with every GSM Interceptor. |
| The process is extremely simple to perform; although mastering it is technically equally advanced. The agent must be within a suitable distance of the targets GSM phone (a one time only operation per number).
You need only to know the targets phone number, then send out a ping to the targets GSM phone. The phone will never activate or make a ring signal, as the ping takes only milliseconds to perform. However, the targets phone will reply with specific data, including the encrypted KI code.
You then need to stay in the local area a short while so as to sample the network.
This data is then decrypted, making use of our radically new hardware and special software. This process is done in real time.
The unit now knows the telephone number, IMEI and the KI code, and enters this data into the memory of the main GSM Interceptor unit.
Whenever the operator needs to intercept the targets calls, he simply flags the relevant telephone number with the linked KI code. From that moment on the system will can intercept all incoming and outgoing calls.
|
| |
| SMS, Fax & Email
mode |
| The system will allow the operator to read (SMS) Short Message Service sent to and from targets phone. Also faxes are fully readable, as well as email accessed by target.
As an example the operator will be able to see targets banking codes and pin numbers if he uses the cell phone for accessing his account.
|
| |
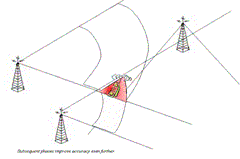
| Tracking of the Target Location |
| Making use of the newly designed software specially made for this application, the GSM Interceptor will allow the operator to track the target internationally.
This is done by triangulating the location of the cell phone via the existing base stations.
In city areas, where the base stations are numerous, the typical accuracy is +- 2 meters.
In rural areas where the base stations are fewer, typical accuracy can be +- 100 to 250 meters.
So provided the operators digital mapping system is on a scale of 3000 to 5000:1, the accuracy is extremely high. Using this technology, the problems that GPS need to see clear sky is no longer an obstacle to the operator. It will display the targets location outside as well as inside buildings.
|
 |
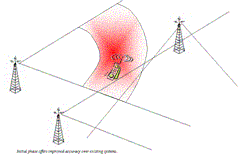 |
| This feature alone can be of vital importance in many scenarios, adding security to the agents involved in the visual surveillance of target.
The tracking system will work internationally, so even if the target is traveling to another country the operator will see the exact location in real time.
The tracking feature is constantly running in the background of the intercept program, as long as targets phone is switched on.
|
| |
| Intercept calls made in another country |
| This new feature is a very dramatic development. It allows the operator to intercept calls made to and from the targets cell phone regardless of location. As long as the target is using his GSM network to make or receive calls the GSM Interceptor will intercept.
|
|
|
|
|
|